Business leaders at any level understand the importance of protecting their company’s assets and information. Cybersecurity is not an optional extra, but a critical component of protecting their business. Cyber-attacks are becoming more frequent and sophisticated, and businesses of all sizes are at risk. In fact, a study found that cyber-attacks cost businesses an average of $3.86 million in 2020.
So, why do you need cybersecurity? Here are three key reasons:
- Protect Your Company’s Reputation and Financial Health – A cyber-attack can have devastating consequences for your company’s reputation and financial health. If your customers’ data is compromised, they may lose trust in your company and take their business elsewhere. Additionally, you may face fines and legal action if you fail to comply with data protection regulations.
- Safeguard Your Intellectual Property – Your company’s intellectual property is a valuable asset that needs to be protected. Cybercriminals can steal your trade secrets, patents, and other proprietary information, which can have a significant impact on your business.
- Mitigate Operational Disruption – A cyber-attack can disrupt your company’s operations, resulting in lost productivity, downtime, and even data loss. This can be especially damaging given that most companies rely on technology to deliver their products and services.
An Effective Cybersecurity Methodology
To ensure that your company is adequately protected, it’s important to have an effective and trusted partner with a solid cybersecurity methodology.
An effective methodology generally consists of four key stages with critical actions and milestones tied to each:
- IDENTIFY vulnerabilities through a complete Network Assessment and Vulnerabilities Management plan.
- PROTECT your assets with Security Education Training & Awareness (SETA) and Compliance services.
- DETECT threats through Endpoint Detection & Response (EDR) and Dark Web Monitoring.
- OPTIMIZE your security posture with Penetration Testing and a Managed Security Operations Center (SOC).
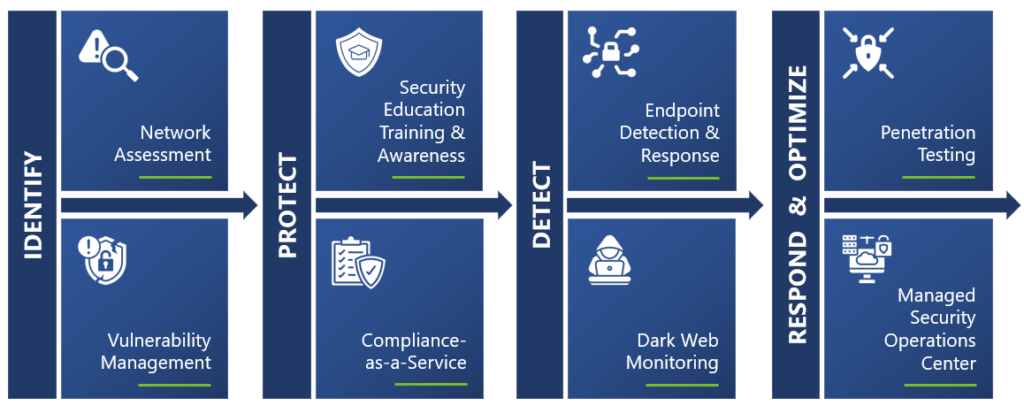
This methodology allows your organization to identify potential vulnerabilities, protect your systems and data, detect and respond to threats in real time, and continuously optimize your cybersecurity posture.
Cybersecurity Services
It’s important to choose a partner that offers a comprehensive suite of services designed to keep your company safe from cyber threats.

Network Assessment & Vulnerabilities Management
A Network Assessment is a comprehensive analysis of your organization’s network infrastructure, security architecture, and policies to identify potential security vulnerabilities, gaps, and risks that may expose your network to cyber-attacks. This assessment is a critical step in understanding your security posture and developing a plan to address any vulnerabilities that may exist.
A Network Assessment is critical for a business because it provides a comprehensive evaluation of the security posture of your network infrastructure. It allows you to identify and address potential vulnerabilities and risks before they can be exploited by cybercriminals.

Endpoint Detection & Response
Endpoint Detection and Response (EDR) is a security solution that is designed to protect devices such as laptops, desktops, and servers from cyber threats. EDR involves the deployment of software agents on endpoints that continuously monitor and analyze endpoint activity for potential security threats.
EDR is important for businesses because it provides threat detection, rapid response, proactive protection, compliance with regulatory requirements, and peace of mind knowing that endpoints are being monitored and protected from cyber threats. By deploying EDR, businesses can reduce the risk of data breaches and other security incidents, protecting their reputation and bottom line.
Managed Security Operations Center
A Managed Security Operations Center (SOC) is a service that provides businesses with 24/7 monitoring and management of their cybersecurity systems, including security information and event management (SIEM), intrusion detection, and incident response. It is like a security control room that continuously monitors the business’s network and systems for any signs of cyber threats or attacks.
A Managed SOC is a 24/7 security monitoring and incident response service that helps businesses to detect and respond to cyber threats quickly and effectively. By outsourcing their security monitoring and incident response to a Managed SOC, businesses can benefit from continuous monitoring, real-time analysis, incident response services, proactive protection, and cost-effectiveness. This helps to reduce the risk of data breaches and other security incidents, protecting a business’s reputation and bottom line.

Security Education Training & Awareness
Security Education Training & Awareness (SETA) is a program that is designed to educate employees on how to recognize and respond to cyber threats. It involves providing training and awareness to employees on the importance of cybersecurity and how to identify potential cyber threats.
SETA is important for businesses because it helps to educate employees on how to recognize and respond to cyber threats, protect sensitive data, comply with security policies, and create a security culture within the organization. By providing employees with the knowledge and tools to prevent cyber-attacks, businesses can reduce the risk of data breaches and other security incidents.

Compliance-as-a-Service
Our Compliance-as-a-Service (CaaS) offering helps businesses to achieve and maintain compliance with regulatory requirements and industry standards. It is like having a compliance expert on staff but without the high costs associated with hiring one full-time.
CaaS is a service that helps businesses to achieve and maintain compliance with regulatory requirements and industry standards. By outsourcing their compliance needs to a CaaS provider, businesses can benefit from customized services, specialized knowledge, and cost-effectiveness. This helps to reduce the risk of regulatory fines and other penalties, protecting a business’s reputation and bottom line.

Penetration Testing
Penetration Testing is a security assessment process that involves testing a company’s IT infrastructure, applications, and network for vulnerabilities that attackers could exploit to gain unauthorized access. The testing is performed by a trained security professional who simulates a real-world attack on the business’s systems, applications, and network.
Penetration Testing is an important step for keeping businesses secure because it helps to identify vulnerabilities, test security controls, improve security posture, comply with regulatory requirements, and provide peace of mind. By performing regular Penetration Testing, businesses can reduce the risk of data breaches and other security incidents, protecting their reputation and bottom line.

Dark Web Monitoring
Dark Web Monitoring is a cybersecurity solution that involves monitoring the dark web for any stolen or compromised business data. The dark web is a part of the internet that is not easily accessible by regular search engines, and it is often used by cybercriminals to buy and sell stolen information, such as login credentials, credit card information, and personal data.
Dark Web Monitoring is critical for businesses to consider because it helps to identify stolen data, mitigate risk, protect reputation, comply with regulatory requirements, and provide proactive protection against emerging threats. By deploying Dark Web Monitoring, businesses can reduce the risk of data breaches and other security incidents, protecting their reputation and bottom line.
Safeguard Your Business with a Trusted Cybersecurity Partner
By working with a trusted cybersecurity services partner like Abel Solutions, you can safeguard your reputation, intellectual property, and operational continuity. Contact us today to learn more about our services and how we can help you protect your business.