Imagine a workplace where every employee is vigilant against cyber threats, a place where security isn’t just a protocol but a mindset. In the era of hybrid work, achieving this vision is not just ideal — it’s a necessity.
While implementing security controls and tools is crucial, the true strength lies in empowering your workforce to prioritize security. Without their buy-in, even the most advanced defenses can be rendered ineffective.
Building a security-first culture in a hybrid work environment is complex but achievable. It requires a comprehensive cybersecurity strategy that involves and empowers your workforce. Let’s explore how to create such a strategy.
Critical Components of a Robust Cybersecurity Strategy
Here are the critical components that can take your cybersecurity strategy to the next level:
Perimeter-less Technology
In a hybrid work model, employees work from various locations and collaborate online, which means upgrading your security systems to match the demands of this environment type.
Invest in cloud-based Software-as-a-Service (SaaS) applications that are accessible from anywhere. Ensure your applications support Zero-Trust architecture, a security concept centered on the belief that organizations should not automatically trust anything inside or outside their perimeters. Instead, they must verify anything and everything trying to connect to their systems before granting access.
For example, Microsoft 365 (M365) productivity and collaboration tools can be accessed from any device and location. M365 supports Zero-Trust security by using Azure Active Directory, Microsoft Endpoint Manager, and Microsoft Defender to authenticate, manage, and protect users and devices. With M365, employees can work securely and efficiently from anywhere, while the organization can maintain control and visibility over its data and resources.
Documented Policies and Procedures
Document your security policies and procedures to ensure enforcement. Without documentation, staff may not understand the purpose or steps involved, leading to a lack of buy-in.
Identify critical IT policies and procedures, document them, and share them with the relevant teams and staff. Keep the files up-to-date and accessible. Review policies periodically and make changes as needed.
You can use SharePoint Online to create a site for your security policies and procedures, and grant access to the relevant teams and staff. You can also use SharePoint Online to create workflows, alerts, and approval processes to automate and streamline your documentation process.
Security Awareness Training Programs
Make your employees the first line of defense against cyberattacks. Set up interactive training programs to defend against phishing, ransomware, brute-force password attacks, and social engineering.
Create training videos and a comprehensive repository dedicated to security protocols and SOPs. Reinforce learning with routine tests and simulations.
You can use Microsoft Defender for Office 365, or a similar tool like KnowBe4, to run attack simulations and measure your staff’s response to phishing emails.
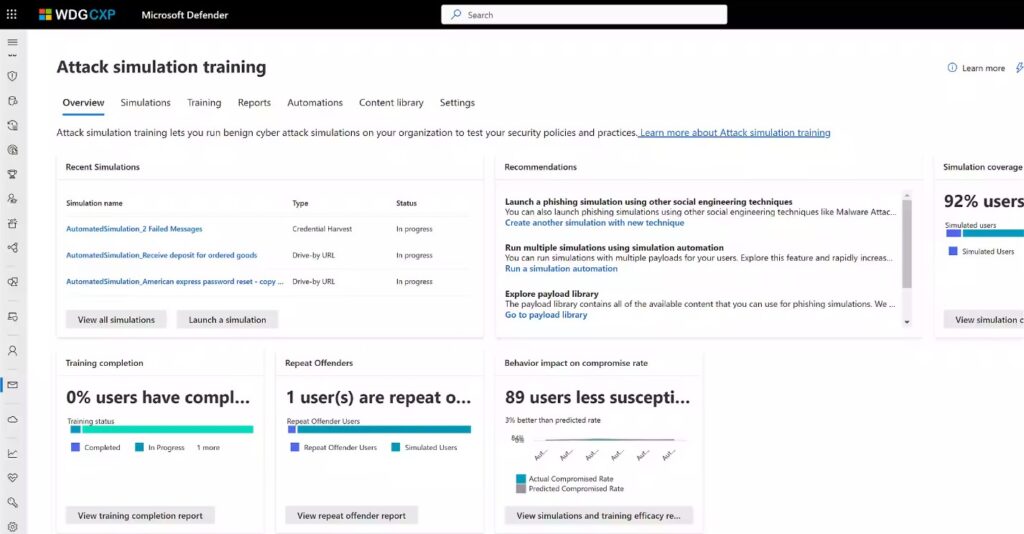
Communication and Support Channels
Define communication and support channels to handle threats effectively. Ensure every staff member knows how to raise an alarm, whom to contact, and what to do after reporting it.
Outline approved tools for communication and collaboration, discouraging personal apps for official use.
For example, you can set up a dedicated security channel in Microsoft Teams where staff can report incidents and get support from IT experts.
Friction-free Systems and Strategies
When devising new security strategies or evaluating systems, prioritize user experience and efficiency. Ensure security measures and policies don’t feel like extra work, or employees may abandon security best practices. Align security systems and strategies with workflows for a seamless experience.
For example, you can use Microsoft Endpoint Manager to manage and secure devices across different platforms and locations. You can enforce security policies, monitor device health, and remotely wipe data if a device is lost or stolen.
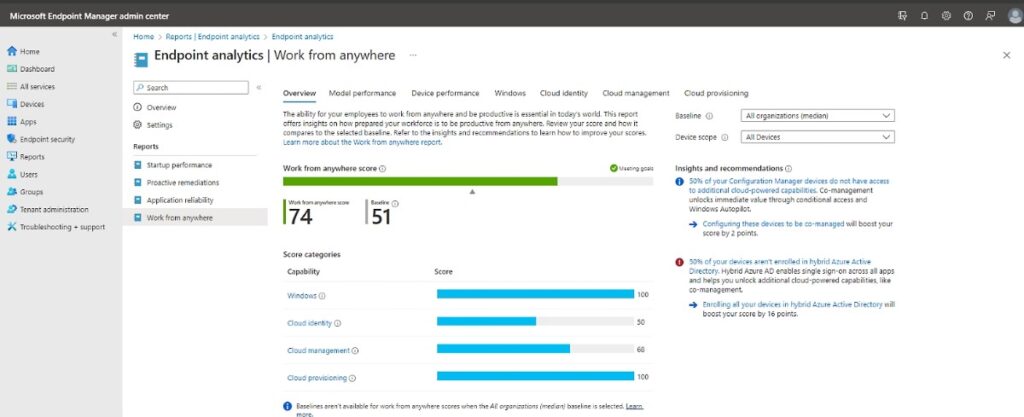
Next steps
Building a security-first culture is challenging, especially in a hybrid work environment. You will need skilled staff, 24/7 support, and specialized tools to succeed.
But you don’t have to navigate this alone.
Our team can guide you through implementing and managing cybersecurity and data security controls. Don’t wait for a breach to happen — proactively secure your business. Contact us to set up a no-obligation consultation and take the first step towards a secure future.