4 Business Benefits of Implementing the Principle of Least Privilege
Many businesses don’t realize it, but employees, vendors and even software applications often have more access than they need. This might seem harmless until a…
Navigate the complexities of cybersecurity and emerge with a robust, high-performance defense system that evolves with the ever-changing threat landscape.

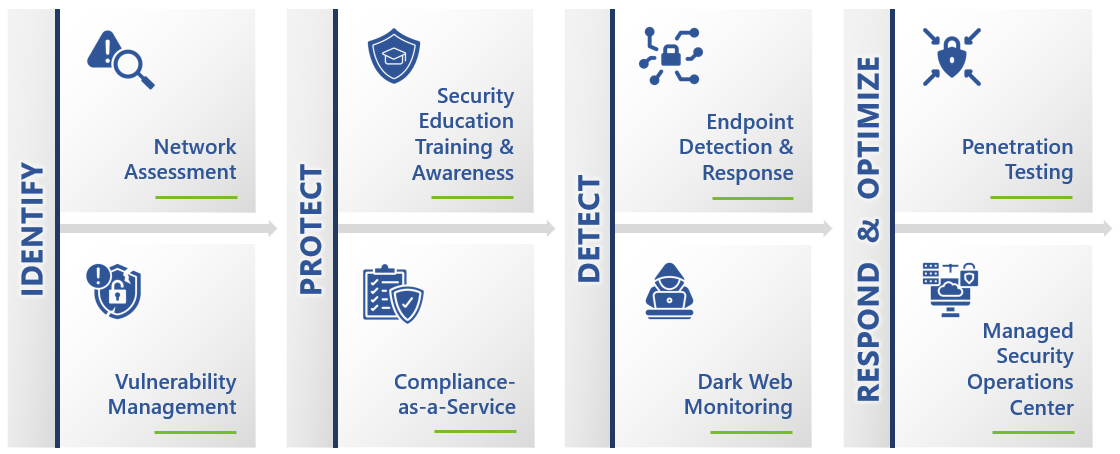
At the heart of our Cybersecurity-as-a-Service lies a four-step methodology, based on the NIST Cybersecurity Framework (CSF) and designed to fortify your digital assets and ensure a resilient security posture.
Our approach encompasses:
IDENTIFY: We begin by meticulously mapping out your digital landscape to pinpoint critical assets, assess potential vulnerabilities, and prioritize security needs.
PROTECT: Implementing robust defenses, we safeguard your systems with cutting-edge security measures tailored to your unique business requirements.
DETECT: Our vigilant monitoring systems stand guard around the clock, swiftly detecting any suspicious activity to prevent breaches before they occur.
RESPOND & OPTIMIZE: In the event of a security incident, our rapid response team is equipped to neutralize threats, while continuously refining our strategies for optimal protection.
1


Keeping track of all the endpoints, printers, network devices, servers, and IoT devices on a growing business’ network is critical to organizational health. If you do not constantly monitor your network, cybercriminals can rush to exploit it. Proper assessment is essential to manage the risks and threats to your network.
Our Network Assessment services automate routine scanning and report generation to give us a constant 360º view of your network. And because every client environment is different, we customize support ticket triggers to troubleshoot issues immediately and keep your data safe.
Our Vulnerability Management Program is a continuous check on exploitable gaps in security infrastructure that cybercriminals leverage to bypass security controls, such as:
We build an inventory of all your organizational assets and then prioritize them based on their value to business operations. This ensures that we assess risks, report risks, then verify their elimination as efficiently and proactively as possible.
2

Over the last two years, Phishing has become the primary vector for data compromise. Cybercriminals focus much of their time on Social Engineering before transitioning into technical escalation. Consequently, that is where an in-depth Security Education Training & Awareness (SETA) program comes into play—giving every user equal opportunity to identify and report Social Engineering attacks.
We provide security awareness training modules for your employees, simulate Phishing campaigns, then provide reporting on organizational progress as well as help pinpoint any employees who need additional training.
Every State in the US is adopting its own Data Privacy and Regulation Laws around how businesses should protect their citizens’ data. A layer above that are the ever-evolving Federal requirements for businesses to follow industry best practices around Information Security.
Compliance-as-a-Service helps keep your organization ahead of the curve by automating compliance assessment, management, and documentation, saving time and preventing costly violations.
3


Our Endpoint Detection and Response (EDR) is an Enterprise Grade Anti-Virus that leverages Artificial Intelligence to detect and respond to security incidents at the endpoint level, such as company desktops, laptops, and servers.
Our solutions are designed to be lightweight and non-intrusive, can be deployed on-premises or in the cloud, and protect against advanced persistent threats (APTs) and other sophisticated attacks. Our services include:
Social Engineering is often accomplished in an automated and scripted manner. Cybercriminals are looking to quickly turn a profit from the credentials they can steal. And all these transactions happen on the Dark Web.
When an organization’s credentials are compromised, it is imperative to receive that signal. The moment an organization’s credentials are listed for sale, an alert is fired back to us, and the investigation begins.
We scour dark web markets, data dumps, and other sources to uncover any compromised credentials and promptly alert you to any security incident, giving you a crucial advantage in acting before cybercriminals do.
4

Our Managed Security Operations Center (SOC) supplies your organization with a centralized team of cybersecurity experts dedicated to 24/7/365 monitoring of security systems, threat intelligence analysis, threat detection and response, and incident response.
Our security professionals’ advanced analytics help us anticipate and prevent attacks before they start, as well as identify and respond to security incidents immediately in real-time.
A SOC eliminates the need for your organization to invest in the costly infrastructure, technologies, and skilled personnel required to build and operate cybersecurity management
in-house.
After an organization has reached a stepstone in security maturity, it is imperative that an unbiased party performs checks on control performance. By leveraging Penetration Testing (PenTest), an organization identifies areas that are weaker than others and most prone to cybercriminals.
We will test existing cybersecurity posture, identify vulnerabilities, gauge organizational and regulatory compliance, then create a roadmap for necessary improvements.
|
SILVER Designed for small teams to effectively manage fundamental cybersecurity |
GOLD Perfect for businesses that require a comprehensive security solution |
PLATINUM Ideal for businesses with ambitious growth plans & a strong security focus |
|
|---|---|---|---|
| Starts at $25/asset/month | Starts at $40/asset/month | Contact us for pricing details | |
| Included Capabilities | |||
| Vulnerability Management | |||
| Endpoint Detection & Response | |||
| Dark Web Monitoring | |||
| Managed Security Operations Center | |||
| Network Assessment | |||
| Security, Education,Training & Awareness | |||
| Continuous Threat Hunting 24/7/365 | |||
| Compliance-as-a-Service | |||
| Cloud Security Posture Development & Management | |||
| Managed Log Monitoring | |||
| Included Professional Services | |||
| Security Helpline | |||
| Incident Response | |||
| Virtual CISO & Engineering Services | N/A | 10 hours* | 20 hours* |
| Add-On Professional Services | |||
| Forensic Investigations | Available for an additional charge based on needs | ||
| Penetration Testing | Available for an additional charge based on needs | ||
* Hours are billed at a discounted hourly rate based on services agreement.
Many businesses don’t realize it, but employees, vendors and even software applications often have more access than they need. This might seem harmless until a…
How Proactive Cybersecurity Could Have Prevented a Data Breach What one company’s breach teaches us about the high cost of reactive cybersecurity—and how to avoid…
Most businesses today depend on third-party partners. These partners may provide products, services, or even expertise that help keep your business running and help you…
Despite believing they were immune, a small law firm in Maryland fell victim to a ransomware attack, exposing sensitive and confidential client information. Similarly, an…
Imagine starting your day with a cup of coffee, ready to tackle your to-do list, when an email that appears to be from a trusted…
Imagine a workplace where every employee is vigilant against cyber threats, a place where security isn’t just a protocol but a mindset. In the era…
As the world is becoming more digitized every day, cybersecurity is non-negotiable. What if there was a way to bolster your defenses against cybercriminals by…
As technology continues to evolve, so do the threats that businesses face. Cybersecurity is a critical concern for any organization, and regular security testing and…
In today’s interconnected world, cybersecurity is no longer a mere technical afterthought; it’s a strategic imperative for every business. Cyberattacks can bring your operations to…
The rise of AI has sparked a revolution. Everyone, from industry giants to smaller enterprises, is captivated and eager to leverage AI’s endless possibilities. AI…
Sensitive company data—like employee emails and passwords—could be on the dark web for months before you realize there’s been a security breach. The first step in bolstering your cybersecurity posture is to identify what company data has already been compromised.
Our cybersecurity experts leverage state-of-the-art Dark Web diagnostics to uncover what company data is currently circulating amongst bad actors.
Fill out the form to request your free Dark Web scan and we’ll deliver results to your inbox within 1-2 business days.