Over the past decade, we’ve seen a significant shift in corporate compliance. Governments have launched new and unprecedented regulations while also enforcing old rules with renewed vigor. And an explosion of communications channels—from social media to collaboration platforms like Microsoft Teams—means there are many more ways rules can be violated.
To protect your company, you must ensure that you have the right technologies and processes in place to keep up with all of the rapidly evolving laws, regulations and standards that apply to your organization and industry. Failing to be aware of and adhere to these rules can result in costly fines or even lawsuits.
 At its core, compliance means adhering to a particular set of rules. As an organization, you must always be aware of and take steps to comply with the relevant specifications, policies, standards and laws to achieve regulatory compliance related to your business or industry. It’s also important to consider that compliance for your business may include both internal policies and procedures, as well as laws and regulations enforced at the federal or state level.
Some of these regulations are well known—like the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA compliance requires that the healthcare industry take steps to assure that individuals’ health and private information are adequately protected. Other regulations may be less obvious—such as the recent Cybersecurity Maturity Model Certification (CMMC), which impacts a wide range of government contractors across hundreds of thousands of companies in the supply chain.
At its core, compliance means adhering to a particular set of rules. As an organization, you must always be aware of and take steps to comply with the relevant specifications, policies, standards and laws to achieve regulatory compliance related to your business or industry. It’s also important to consider that compliance for your business may include both internal policies and procedures, as well as laws and regulations enforced at the federal or state level.
Some of these regulations are well known—like the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA compliance requires that the healthcare industry take steps to assure that individuals’ health and private information are adequately protected. Other regulations may be less obvious—such as the recent Cybersecurity Maturity Model Certification (CMMC), which impacts a wide range of government contractors across hundreds of thousands of companies in the supply chain.
 Here are some of the compliance regulations we help our customers meet every day.
Here are some of the compliance regulations we help our customers meet every day.
What is the definition of compliance as it relates to business?
 At its core, compliance means adhering to a particular set of rules. As an organization, you must always be aware of and take steps to comply with the relevant specifications, policies, standards and laws to achieve regulatory compliance related to your business or industry. It’s also important to consider that compliance for your business may include both internal policies and procedures, as well as laws and regulations enforced at the federal or state level.
Some of these regulations are well known—like the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA compliance requires that the healthcare industry take steps to assure that individuals’ health and private information are adequately protected. Other regulations may be less obvious—such as the recent Cybersecurity Maturity Model Certification (CMMC), which impacts a wide range of government contractors across hundreds of thousands of companies in the supply chain.
At its core, compliance means adhering to a particular set of rules. As an organization, you must always be aware of and take steps to comply with the relevant specifications, policies, standards and laws to achieve regulatory compliance related to your business or industry. It’s also important to consider that compliance for your business may include both internal policies and procedures, as well as laws and regulations enforced at the federal or state level.
Some of these regulations are well known—like the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA compliance requires that the healthcare industry take steps to assure that individuals’ health and private information are adequately protected. Other regulations may be less obvious—such as the recent Cybersecurity Maturity Model Certification (CMMC), which impacts a wide range of government contractors across hundreds of thousands of companies in the supply chain.
Compliance regulations across industries
It’s safe to say that no matter your industry, there are likely compliance regulations in effect. Consider data privacy, for example. According to Gartner1, by 2023, 65% of the world’s population will be covered under privacy regulations (up 10% from today). Here are some of the compliance regulations we help our customers meet every day.
Here are some of the compliance regulations we help our customers meet every day.
PCI Compliance
The Payment Card Industry (PCI) Data Security Standards (DSS) is a global information security standard designed to prevent fraud through increased control of credit card data. Organizations of all sizes must follow PCI DSS standards if they accept payment cards from the five major credit card brands – Visa, MasterCard, American Express, Discover, and the Japan Credit Bureau (JCB). PCI compliance is required for any organization that stores, processes or transmits payment and cardholder data.HIPAA Compliance
HIPAA is a federal law that enforces national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge. Healthcare organizations who fall short in their compliance obligations could face penalties ranging from $100 to $50,000 per violation involving data breach.SOX Compliance
The United States Congress passed the Sarbanes-Oxley Act of 2002 (SOX) to provide security for consumers and the general public against corporations acting maliciously or carelessly. The requirements of SOX compliance ensure that companies are transparent about financial reporting and follow the official rules that are in place to prevent fraud. While public companies are required to comply with SOX financially and in Information Technology (IT), it is also considered best practice for non-publicly traded companies to follow SOX compliance regulations.GDPR Compliance
The General Data Protection Regulation (GDPR) is a regulation in EU (European Union) law on data protection and privacy in the EU and the European Economic Area (EEA). It addresses the transfer of personal data outside the EU and EEA areas. The GDPR’s primary aim is to give individuals control over their personal data and simplify the international business’s regulatory environment by unifying the regulation within the EU. Since the implementation of GDPR, we continue to see more data privacy regulations passed across the world and in the United States. California’s Consumer Privacy Act (CCPA), modeled on GDPR, took effect in January 2020, and according to Gartner, at least 13 other states have passed similar laws impacting nearly 40% of the U.S. population.CMMC Compliance
Initially released in early 2020, the Cybersecurity Maturity Model Certification (CMMC) is the Department of Defense’s (DoD’s) response to significant compromises of sensitive defense information located on contractors’ information systems. Establishing a unified standard for implementing cybersecurity across the defense industrial base (DIB), the CMMC applies to over 300,000 companies in the supply chain (including small businesses, commercial item contractors and foreign suppliers). The DoD has taken a “crawl, walk, run” approach to implementing CMMC, but plans to have it fully deployed by 2027.What About Compliance in the Cloud?
When working with organizations of all sizes and across all industries, we frequently hear concerns about adhering to compliance regulations in the cloud. Let’s debunk a few common myths when it comes to compliance in the cloud.Myth #1 – The cloud isn’t as secure as on-premises environments and therefore can’t be compliant.
This was a commonly held myth in the early days of cloud-based services. You often heard stakeholders say that they didn’t “trust the cloud.” There was a belief that because they couldn’t put their hands on the hardware and couldn’t see everything that was happening behind the scenes, it couldn’t be trusted. In the early days, with the rapid rise of cloud-based services and the lack of standards in place, the concerns weren’t entirely unfounded. Cloud services were often not transparent in explaining their posture on data security, internal development standards, or what measures they employed to help customers meet compliance regulations. The industry has stabilized significantly over the last decade, and transparency in these areas has become something that cloud service providers, like Microsoft, now lead with when selling their services. Microsoft makes it a point to let potential customers know all of the standards their service meets and the process by which they test their systems to make sure safeguards are working as intended. This transparency makes trusting cloud-based services much more straightforward and should be something that stakeholders look for when evaluating a cloud-based service for their organization.Myth #2 – We’re a small organization, so we can’t do all of this.
Compliance can be daunting, both to understand conceptually, to implement and to manage on a day-to-day basis. Fortunately, cloud-based services can help ease this burden. By taking the time to understand how a particular service handles processes that may impact your organization’s compliance regulations and which controls and features they may offer that pertain to compliance, you can develop a plan to both mitigate risk and gain visibility into new areas of concern within your business before they arise.Myth #3 – We use services from major providers, and they take care of everything.
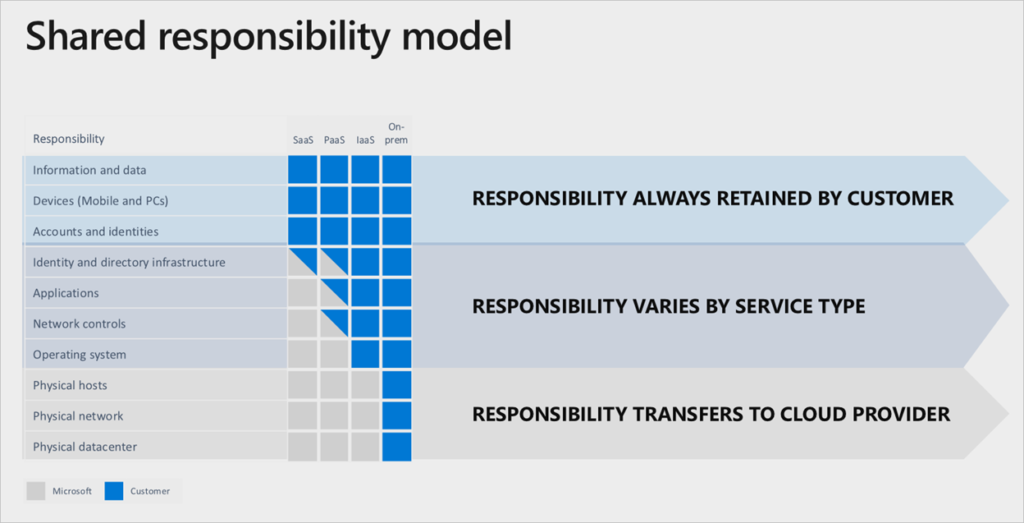
In an on-premises or private data center environment, you generally own everything and have complete responsibility for all security and compliance requirements. Public cloud services, such as Microsoft 365, Microsoft Azure and Amazon Web Services (AWS), provide a wealth of convenience when it comes to compliance. Each has already achieved certifications to meet global compliance requirements – such as ISO 27001, PCI DSS, HIPAA, and FedRAMP – and provide numerous methods to help businesses deal with aspects of the service under compliance regulations. Many organizations mistakenly assume that they take a lesser role in security and compliance once they move to cloud-based services. To protect your organization from liability, you should understand the Shared Responsibility Model commonly used by cloud service providers.Shared Responsibility in the Cloud
A Shared Responsibility Model dictates who is responsible for which aspects of security and compliance when using a particular cloud service model. While the details can shift depending on the type of service being used (e.g, Saas, PaaS, Iaas, etc.), you can usually simplify it as follows:- The Cloud Service Provider (CSP) is responsible for the security OF the cloud.
- The service user (your company) is responsible for security and compliance IN the cloud.
Technologies That Support compliance in the Cloud
Email Encryption
Ensuring that emails containing sensitive information can be viewed only by the intended recipient is a critical component of several compliance regulations. Many encryption systems can detect specific types of content and enforce encryption automatically, removing the burden from employees.Email Archiving
Many compliance regulations and some state regulations require that an organization maintain immutable copies of all sent and received emails for a specified period. Email archiving solutions help an organization accomplish this while providing easy search and recovery capabilities if something is needed.Secure File Share
Most modern email systems have severe restrictions on the size and type of content that can be emailed. Secure file sharing services allow users to send and receive files safely and securely by allowing expiration data, audit tracking and alerting.Data Compliance/DLP/Data Classification Policies
Allowing certain types of data such as Social Security and credit card numbers to be transmitted outside of your organization is an easy way to violate many compliance regulations. Data loss prevention (DLP) systems and data classification policies can allow you to both block and be alerted if someone mistakenly attempts to transmit information they shouldn’t.Access and Authentication Logging
Certain compliance regulations require you to maintain detailed authentication and access logs to monitor for potential breaches and provide root cause analysis in the event of a breach.Authentication and Access Controls
Multi-factor authentication is an excellent tool for protecting your organization, but what if someone forgets to enable it? Authentication and access controls can ensure that nothing slips through the cracks while also controlling the locations and systems from which users can access company data.Risk-based Policies
Many systems, such as Microsoft 365, can detect risk events such as someone authenticating from two disparate locations in an unreasonable amount of time or authenticating from a location where they’ve never been. Risk-based policies allow you to enforce reasonable protections if something is happening that may not set off any immediate alarms.How Abel Solutions Can Help With Your Compliance Needs
Our team can help guide you through determining the technology platform and tools that make sense for your business, designing solutions to meet your unique business challenges and navigating through common implementation hurdles to successful adoption.As a Microsoft Gold Partner, we offer Microsoft 365-based solutions to help businesses meet compliance regulations.
Contact us today if you’d like to learn more about implementing email encryption services, creating a long-term strategy for meeting and maintaining compliance regulations, or anything in between.
This Abel Insight was written by Abel Solutions’ Jason Casteel, IT Services Manager.